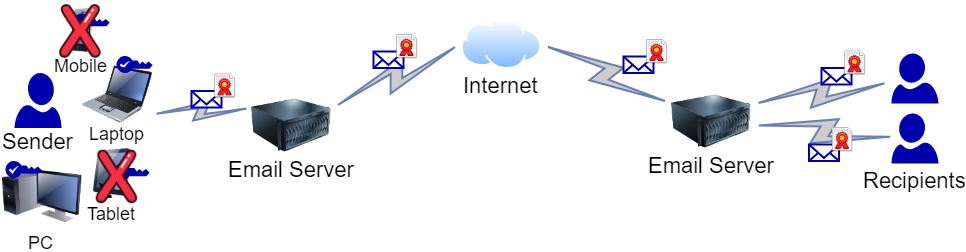
In the ever-escalating battle against malicious spammers,
spoofing and email compromise are becoming harder to combat each day.
Attackers are getting smarter and sending targeted emails that pass many of the standard spam checks such as blacklists or SPF checks. Rightly, people are becoming more suspect of the emails they receive and the supposed sender’s identity.
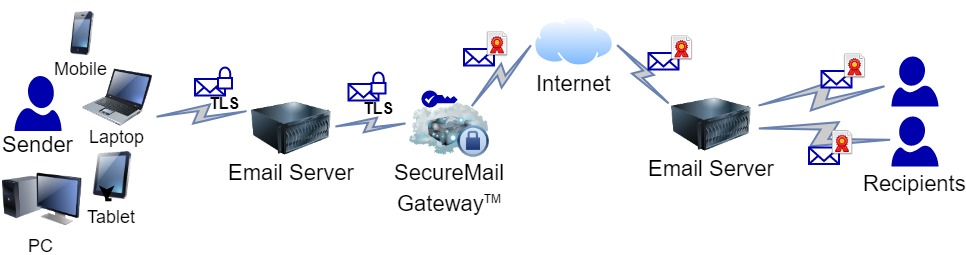
One of the best tools available for ensuring the authenticity of your email is an S/MIME digital signature. It is so powerful in fact that the US Department of Defense (DoD) has required all outgoing emails by DoD personnel to be digitally signed since 2011. Digital signatures not only guarantee the identity of the sender, but also protect the contents of the message from being secretly modified.